How To Install OVFTool on Ubuntu 20.04 with Python3
Since I use terraform to clone and provision VMs on ESXi, I need to use VMWare’s ovftool. However, I’ve been having errors lately. The OVFTool wants to install using python2, and I keep getting syntax errors. Seems like it’s using my Python3 install and I can’t get it to install.
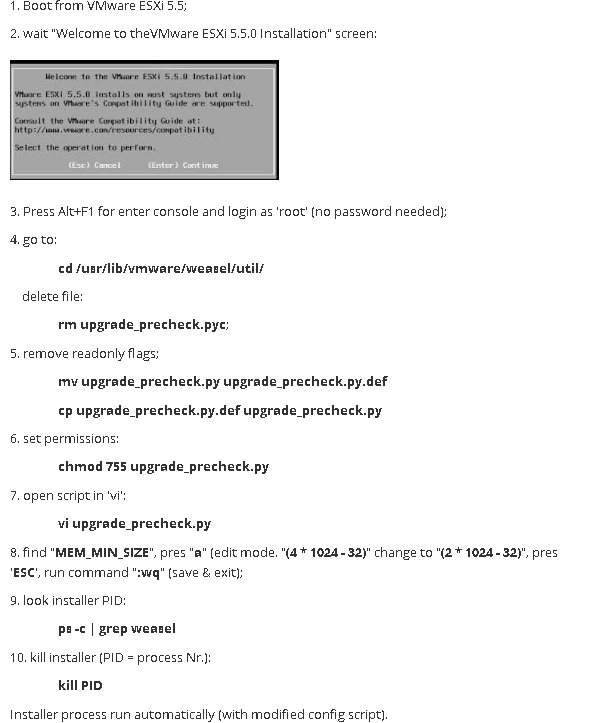
If we cannot install the ovftool via the conventional way, we have to find a detour or a workaround to get there. For this particular issue with the failed installation on Ubuntu 20.04, this means extracting the ovftool files from the installation .bundle, copying them to /usr/bin/ and configure an alias for the ovftool executable.
Execute ovftool without installing it
This is how it works step-by-step:
Extract the files and change into directory ovftool (you can name the extracted directory as you want):
sudo ./VMware-ovftool-4.4.1-16812187-lin.x86_64.bundle --extract ovftool && cd ovftool
ls -rtl total 16K drwxr-xr-x 4 root root 4,0K Mär 9 14:07 . drwxr-xr-x 5 rguske domain^users 4,0K Mär 9 14:07 .. drwxr-xr-x 9 root root 4,0K Mär 9 14:07 vmware-installer drwxr-xr-x 6 root root 4,0K Mär 9 14:07 vmware-ovftool Here’s what’s in it: $ tree -L 2 . ├── vmware-installer │ ├── artwork │ ├── bin │ ├── bootstrap │ ├── lib │ ├── manifest.xml │ ├── python │ ├── sopython │ ├── vmis │ ├── vmis-launcher │ ├── vmware-installer │ ├── vmware-installer.py │ ├── vmware-uninstall │ └── vmware-uninstall-downgrade └── vmware-ovftool ├── certs ├── env ├── icudt44l.dat ├── libcares.so.2 ├── libcrypto.so.1.0.2 ├── libcurl.so.4 ├── libexpat.so ├── libgcc_s.so.1 ├── libgoogleurl.so.59 ├── libicudata.so.60 ├── libicuuc.so.60 ├── libssl.so.1.0.2 ├── libssoclient.so ├── libstdc++.so.6 ├── libvim-types.so ├── libvmacore.so ├── libvmomi.so ├── libxerces-c-3.2.so ├── libz.so.1 ├── manifest.xml ├── open_source_licenses.txt ├── ovftool ├── ovftool.bin ├── README.txt ├── schemas ├── vmware.eula └── vmware-eula.rtf 11 directories, 31 files
Move the vmware-ovftool directory to /usr/bin/:
sudo mv vmware-ovftool /usr/bin/
Make the two files ovftool as well as ovftool.bin executable:
sudo chmod +x /usr/bin/vmware-ovftool/ovftool.bin sudo chmod +x /usr/bin/vmware-ovftool/ovftool
Configure an alias for your used shell to execute it as usual:
alias ovftool=/usr/bin/vmware-ovftool/ovftool
Impactos: 0